Hi there,
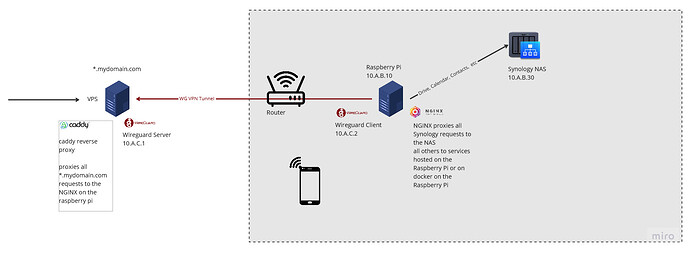
I am running a mini homelab consisting of a Raspberry Pi and a Synology NAS.
I am facing a few challenges, however, I have everything running, I am just not sure whether I overcomplicated things and feel there must be a better solution as well as 1 issue I am unable to resolve.
My background is in IT, but i has been quite a while since I was active in “network things”, so I am a bit rusty when it comes to routing, iptables etc.
What I want to achieve:
I want to be able to access Snyology Drive, Photos, Calendar and Contacts from anywhere in the world from my mobile devices. I also want to access vaultwarden.
I want this to be secure and I don’t want to have to change app configs everytime I leave my LAN (I will get to that in a moment). I do not want to open any ports on my firewall and I do not want to expose my home IP address and ideally want to “own” the entire chain end-to-end i.e. I don’t necessariyl want to have to trust e.g. Cloudflare that they don’t snoop in on connections which is why I avoid Cloudflare Zero Trust Tunnel for example.
Status quo:
I have a VPS set up with a Wireguard Server running on it and caddy as a reverse proxy.
I have a Raspberry Pi set up with a Wireguard Client running.
The RPI also hosts vaultwarden (“native” service), Ad Guard (“native” service as well) as well as a few docker containers e.g. NGINX proxy manager.
Then there is a Synology NAS hosting the usual Synology Drive Server, Photos, Contacts, Calendars etc.
The LAN is a 10.A.B.0/24 network.
Problem(s):
My first problem here was that despite all the tutorials saying “it just works”, it simply didn’t work to point caddy on the VPS to the NAS. It simply doesn’t seem to be able to connect.
I have been wondering (this is where my rustyness comes in) just how it would know that 10.A.B.30 can be reached via 10.A.C.1 - the local wireguard interface.
I tried the same with Cloudflare tunnels where again all the tutorials show it “simply works”, but it doesn’t for me. If the tunnel terminates in a docker container on the docker on the raspberry pi, it is unable to connect to the NAS, despite it having a bridge network.
My solution here was to set up another reverse proxy on the Raspberry Pi.
So, basically I have a reverse proxy on the VPS pointing everything to the reverse proxy on the Raspberry PI.
This is a bit of a Let’s Encrypt challenge to ensure both reverse proxies can issue certificates, but it currently works.
The advantage is that I can use the LAN reverse proxy to ensure that I can configure all the Synology Apps and Caldav and Carddav with SSL and it is always a trusted certificate.
Questions:
- Is this setup “ok” or is it silly/insecure/disadvantageous in any way? I really think that double reverse proxy is not required and it feels very much like a dirty workaround.
- I am really wondering what the problem is why the “this just works” tutorials don’t just work for me. I cannot help but think that I am missing a very basic routing/networking thing here that prevents these setups from working.
- There is one big issue which I was not able to resulve: Synology Drive desktop clients require port 6690 for file sync. I was unable to get this working due to the reverse proxies. Any solution for this?
Wireguard Client config
[Interface]
Address = 10.A.C.2/32
PrivateKey = (hidden)
MTU = 1300
[Peer]
PublicKey = (hidden)
PresharedKey = (hidden)
AllowedIPs = 10.A.C.1/32
Endpoint =(hidden)
PersistentKeepalive = 15
Wireguard Server config
[Interface]
Address = 10.A.C.1/30
ListenPort = (hidden)
PrivateKey = (hidden)
MTU = 1300
PostUp =
PostDown =
[Peer]
PublicKey = (hidden)
PresharedKey = (hidden)
AllowedIPs = 10.A.C.2/32
Thank you in advance.
Best
Stefan