I’m a huge fan of SpaceRex Videos and they have helped jump start my knowledge of Synology. Thanks so much!
I’m an IT professional at a very large corporation (we are not a carrier and have our own class ‘A’ IP address). I’m struggling to understand what interfaces do what and how they function on a Synology NAS. I’m running a NAS with Open VPN server (Local - as a service) and Open VPN client (Remote - native –DSM). My VPN tunnel comes up, but I am unable to map drives, route packets or Ping. When I use Open VPN Windows Client
on the remote side, the tunnel works fine.
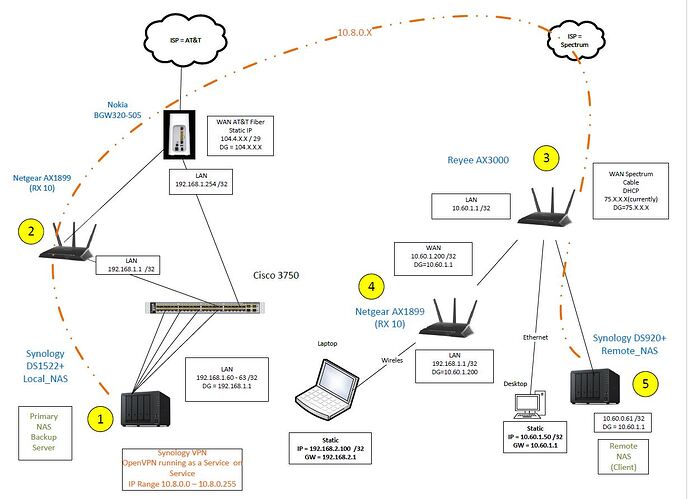
Please seen Network Drawing:
Local Side:
Local NAS 1522+ (Labeled on diagram as (1))
Inside = 192.168.1.60 /32 DG = 192.168.1.1
VPN Server = 10.8.0.0 / 32
Netgear RX 10 Router and A/P (Labeled on diagram as (2))
Inside = 192.168.1.1 / 32
Outside = Static 104.4.X.X /29 DG =104.X.X.X
Carrier = AT&T
Modem / Router = Nokia BGC320-505 (Not Labeled on diagram)
Inside 192.168.1.254
Outside 99.152.X.X DG=99.152.X.X
Remote Side:
Remote NAS 920+ (Labeled on diagram as (5))
Inside = 10.60.1.61 /32 DG = 10.60.1.1
VPN Client 10.8.0.0 /32
Reyee AX3000 Router & A/P (Labeled on diagram as (3))
Inside = 10.60.1.1 /32
Outside 75.X.X.X / DG = 75.X.X.X
Router #2 Netgear RX10 (Labeled on diagram as (4))
Inside = 192.168.2.1 /32
Outside= 10.60.1.200 /32
The remote side has laptop wirelessly connected to the RX10 on 192.168.2.0 /32
The remote side has a desktop Ethernet connected to 10.60.1.0 /32
Remote connectivity functions correctly for both the laptop and desktop when connected via the Windows Open VPN client.
I’m a Cisco CCNA/CCDA/CCNP Voice, so I understand routing (not that I’m above doing something stupid – I do that all the time)!
The Windows firewall is enabled on both windows P.C.’s.
The Firewall and Router services on the 1522+ and 920+ are not enabled.
When the Open VPN windows client is run on a P.C. on the remote side , a route is injected to the other side (local) 192.168.1.0 /32 via 10.8.0.10/32 with GW = 10.8.0.9. (Via Route Print at a CMD prompt)
10.8.0.9 shows up in the ARP Table with a dynamic MAC Address. All the pieces are in place and it works like a champ.
When the Windows Open VPN client is disabled, the route and the dynamic IP Address/MAC address disappear.
What I’m struggling to understand is how the Synology presents interfaces to route table.
Logically the ‘inside’ would be the 192.168.1.0 /32 (local) and 10.60.61 / 32 (Remote). One would think the 10.8.0.0 would be ‘outside’.
Even if I put a static route in the Reyee AX300 (10.60.1.1 / 32) pointing 192.1681.0 /32 to the inside interface of the remote NAS (10.60.1.61) is does not work.
I suspect the NAS at 192.168.1.61 does not know to send the packet going to 192.168.1.0 /32 out the ‘Outside’ 10.8.0.0 /32 interface. Is there a routing protocol used between the two Synology NAS when the Sever/Client connection is up? Does it have it’s own routing table? If so, can it be viewed? If I need to enable routing in the Synology, what order do services process incoming packets in? Is Router First, Firewall Second, VPN third?
Any help with this will be greatly appreciated.
Synology has a fantastic product with the worst support I have ever seen!
I have about 5-6 hours in this with Synology support. They won’t do a voice call, won’t have a manager contact or call me. It’s clear to me my support person does not understand routing. I’m told my case is escaladed, but I still have to deal with the same Tier 1 support person that has had the case for over 3 weeks. All I get is links to non-specific knowledge base articles (that often have nothing to do with the question I asked). I’m starting to believe that Synology support makes AT&T support look good!