Background
Synology has finally added the ability to fully encrypt an entire volume, rather than having to encrypt ever single shared folder. With this it also removed the restriction on having only 143 characters in a file name to get encryption, plus snapshots can now be visible! Great! Right?
Response from Synology
A bug report was filed with Synology about this. The reply was:
Our developer team confirmed that as of now on the DSM 7.2 beta, that this is expected behavior.
That is currently all of the information that I can say or share about this presently.
Updated response:
After posting the video the following comment was posted:
Thanks for the feedback.
This is expected behavior as of the first DSM 7.2 Beta. The responsible team is working on the mechanism to unmount the encrypted volume if a reset is performed. This will prevent access to data on encrypted volumes even if both the system and drives are compromised.
THIS IS GREAT NEWS Turns out that there was a miscommunication between me and Synology! It hopefully will be resolved by 7.2 release.
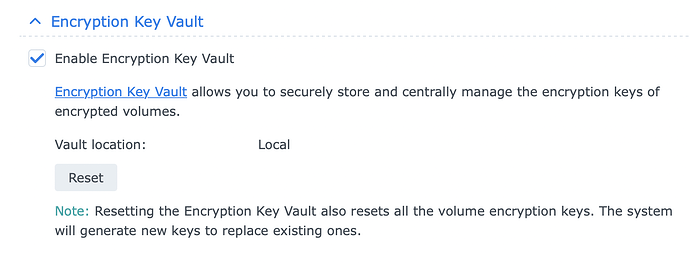
How the Keys are Stored
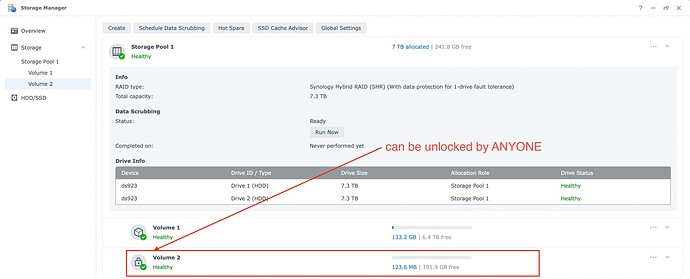
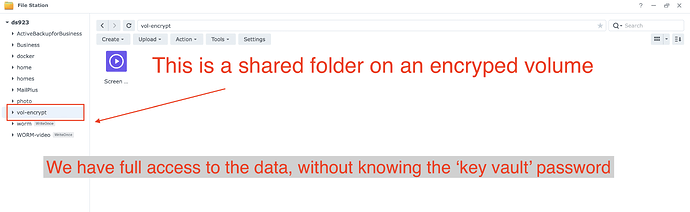
The encryption keys for the volumes are now stored in a Key Vault, which I thought was similar to the key manager used by shared folder encryption. The vault can be stored in one of two places: locally (the default, and what 99% of synologys will use) or KMIP to another Synology (really designed for large businesses). This key vault automatically mounts the volumes on boot, which for volume encryption makes a ton of sense! The problem is it allows anyone with phyical access to the NAS FULL CONTROL
How anyone can steal your “encrypted” data
The encryption keys pretty much do nothing if someone gets physical access to the NAS if stored locally. This is all it takes to steal your encrypted data:
What they need:
- Physical access to the NAS
- A paperclip
Steps to view, edit, or delete your ‘encrypted’ data:
Step 1) Perform a soft reset on the NAS
Take a paperclip or any other thin object and hold the reset button for 6 seconds, release when you hear the first beep. Further info here.
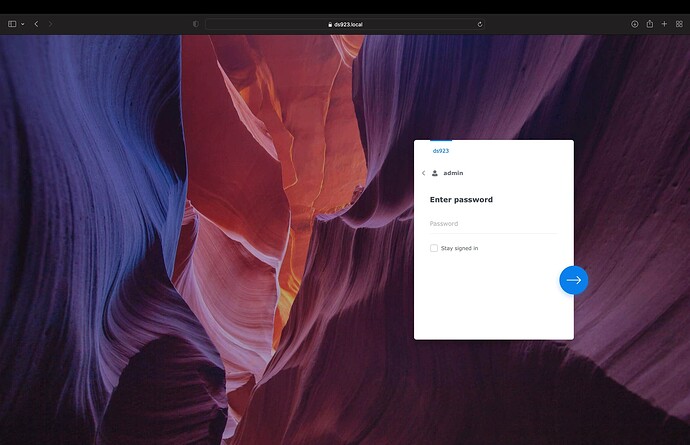
Step 2) Change the password of an administrator
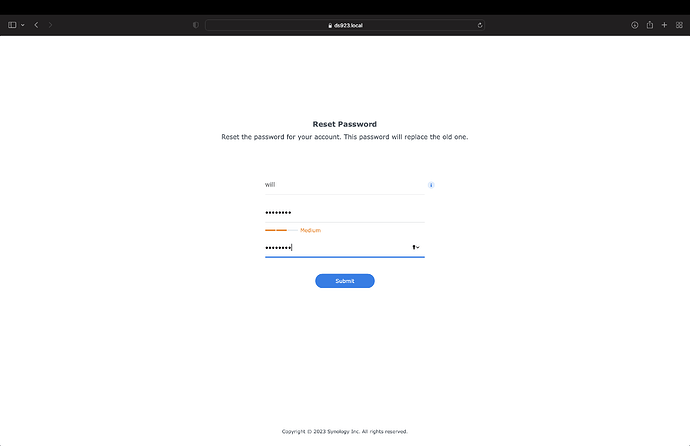
After you do a soft reset you can change the administer password by logging in as the user ‘admin’ with no password
It will then allow you to change the password of any user, so just set the administer account to a password you choose.
Step 3) Login with the password you just changed.
Thats really it. Log in and all the encrypted volumes are still mounted, and will still be mounted after a reboot. You have admin access to all of the data.
My thoughts:
The Key Issue
Encrypting data on a NAS is meant to protect you from physical attack. It is meant to make sure that if someone gets physical access to the NAS and walks away with it that they cannot access the data. In this case, with the default local key store, that is simply not the case.
Soft Reset is NOT the issue
Your first thought might be ‘well Synology should disable the soft reset all together’ this is not the case. The soft reset is really important as it allows users to get into their NAS if they forget their password, or screw up firewall rules. They should be able to access all unencrypted data without issue.
What SHOULD happen
The Key Vault should be stored as a machine key, just like it is with encrypted shared folders. When the NAS is soft reset the machine key is flushed, and has to be reentered to mount any encrypted volumes. This gives the best of both worlds where you can encrypt your data, and have it automatically mount on boot really easily. But if someone walks off with the NAS or the drives, and does not have admin login info, they cant get in!
REMEMBER THIS IS BETA
I want to put this out there as a reminder: this is just the beta version. It’s quite possible that they key manager was not quite ready so they just left it as a local volume for the beta version of this software and it will be real when the full release is out.
Please please Synology fix this before full release
Video going over this:
I have a video coming out 3/15 here that I will link here that shows how this works, and how it SHOULD work